
A Highly Targeted Business Email Scam Causing Big Losses
Key points to share:
What happens if an employee follows through on sending the wire?
Chances are you will never see your money again. The transferred money is usually liquidated immediately after the wire is received on the other end.
Why this scam works?
Employees have busy schedules and are eager to please their boss or a member of senior management without challenging the unusual nature of the request.
Key takeaway:
Ask: Does the request appear reasonable? Is there a sense of urgency to the request? Does the writing style appear awkward?
Authenticate: Email addresses can be spoofed or breached. Know who you are communicating with.
Approve: Have a written procedure in place for approving outgoing wire requests. It's okay to ask questions.
How the scam works:
Cybercriminals are attacking businesses in our area with a twist to the old-fashioned email scam. They’ve discovered the effectiveness of target marketing and personalization. Nationally, the FBI reports that over 8,000 companies have lost an average of $150,000 per incident.
Called the Business Email Compromise (BEC) scam, it starts with a message that appears to be sent from a company’s CEO or CFO to trick employees into wiring money to fraudsters. No business is immune from being targeted, including a bank. In fact, our CFO continues to receive fraudulent emails. We have replicated one of the requests below:
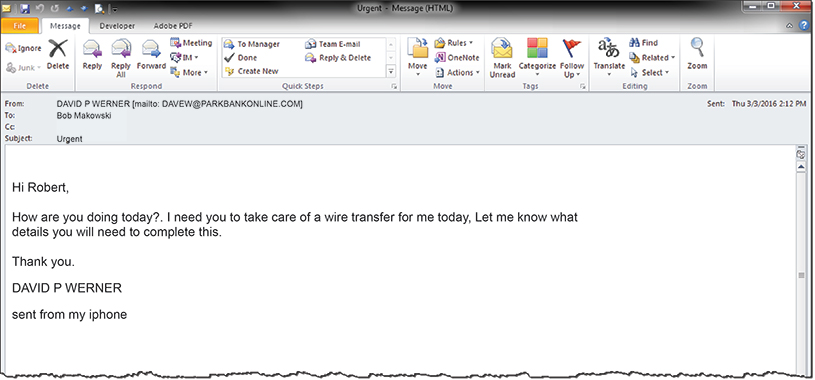
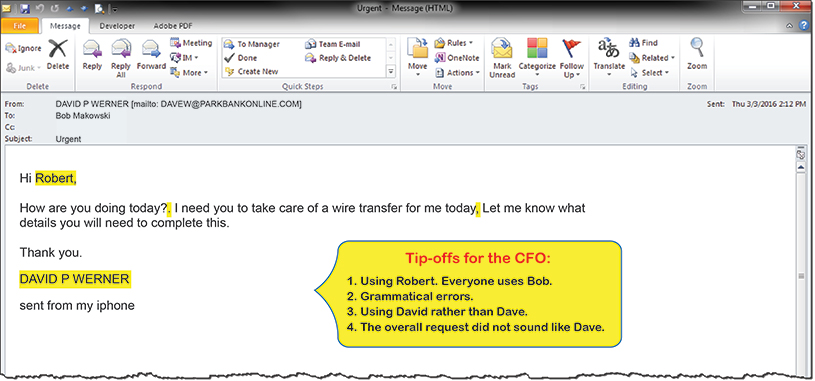
We have seen other fraudulent emails contain all of the specifics of the wire transfer – the beneficiary, the account number, the amount and the ABA number so that the targeted employee had all the information they needed to send the wire without having to verify any information. In our case, our CFO was tipped off to the fake email based on multiple factors.
Increase your employees’ attentiveness to the BEC scam by adopting these five simple-to-implement practices:
- Check to see if the request is consistent with how earlier wire payments have been requested.
- How often does the CEO or CFO directly request a wire payment?
- Are requests typically submitted when traveling? These attacks often are timed when the executive is out of the office
- Is the payment consistent with earlier wire payments – including the timing, frequency, recipient, and country to which prior wires have been sent?
- Verify the identity of the person requesting the funds transfer by using an alternate mechanism.
- If the request is an email, then call and speak to the person using a known phone number to get a verbal confirmation. Or, forward the email (instead of replying) to a known email address. Don’t reply to the email or use the phone number in the email.
- Slow down. Fraudsters gain an advantage by pressuring employees to take action quickly without confirmation of all the facts.
- Be suspicious of requests to take action quickly or email subject lines that include “urgent.”
- Look for grammatical errors or small changes in email addresses that try to mimic legitimate ones, such as abc-company.com vs. abccompany.com or .co vs. com.
- Alert receptionists, administrative support and others not to provide an executive’s travel schedules over the phone to unknown callers or via social media.
- Implement dual approvals for financial transactions. If you do not have written procedures, develop them. Avoid having the two parties responsible for dual approvals in a supervisor/subordinate relationship as it could undermine the effectiveness of the process.
- Use a purchase order model for wire transfers to ensure that all payments have a reference number that can be verified before approval.
Cyber insurance does not necessarily cover losses due to the business email compromise because of an exclusion clause stating there is no coverage for “voluntary parting”, even if the employee was duped. To understand your policy or to inquire about cyber insurance, check with your insurance agent. Source: Bank Investment Daily, www.pcbb.com
This article has been prepared for general informational purposes only and is not intended to be relied upon as professional advice. It is presented without any representation or warranty as to the completeness of the information.

